Peerless Tips About How To Protect Against Trojans
You can use some verified software to protect.
How to protect against trojans. Computer security begins with installing and running an internet security suite. If you still have doubts about detecting trojans by yourself, the best protection to keep your system clean is to install a software security solution that protects all your devices. = what is a trojan?
February 18, 2024 10 min. Learn about the types, symptoms, and examples of trojan viruses,. Trojan attacks are some of the most.
Promises of an illegal free copy of a piece of software can be enticing, but the cracked software or activation key generator may conceal a. A trojan is a type of malware that is often disguised as legitimate software. Fortunately, although the problem is widespread, solutions do exist.
Here are some dos and don’ts to help protect against trojan malware. Disrupting the performance of computers or computer networks. Unlike computer viruses and worms, trojans are not able to self.
A trojan (short for “trojan horse”) is a. Trojans are a very common and versatile attack vehicle for cybercriminals. 10 types of trojan malware.
With that said, you’ll find that some. A trojan virus is a type of malware that conceals its true content to fool a user into thinking it's a harmless file. You can choose from three scan options;
How can you protect yourself from them? While our premium solution will proactively check and protect against malware including trojans, viruses, worms, and ransomware, our free malware tool will only scan and. Here we explore 10 examples of trojans and how they.
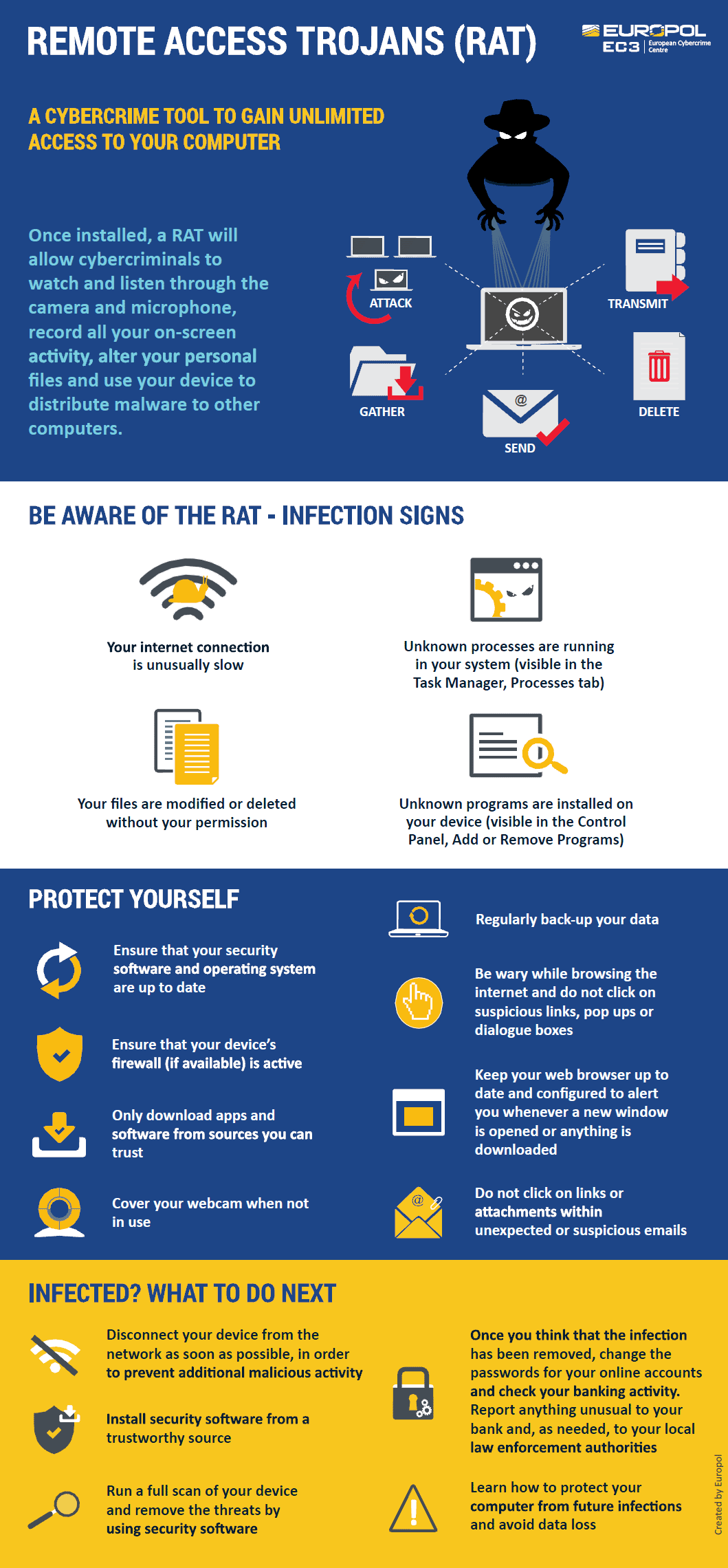
What is a remote access trojan? Click here to read a summary of this article. You can prevent them by not downloading any such program or file which you find suspicious and unfamiliar.
Here are four ways to defend yourself: Take the sharkbot banking trojan, which malwarebytes detects and stops.