Neat Info About How To Detect Ddos

To detect attacks, both types need to be independently monitored;
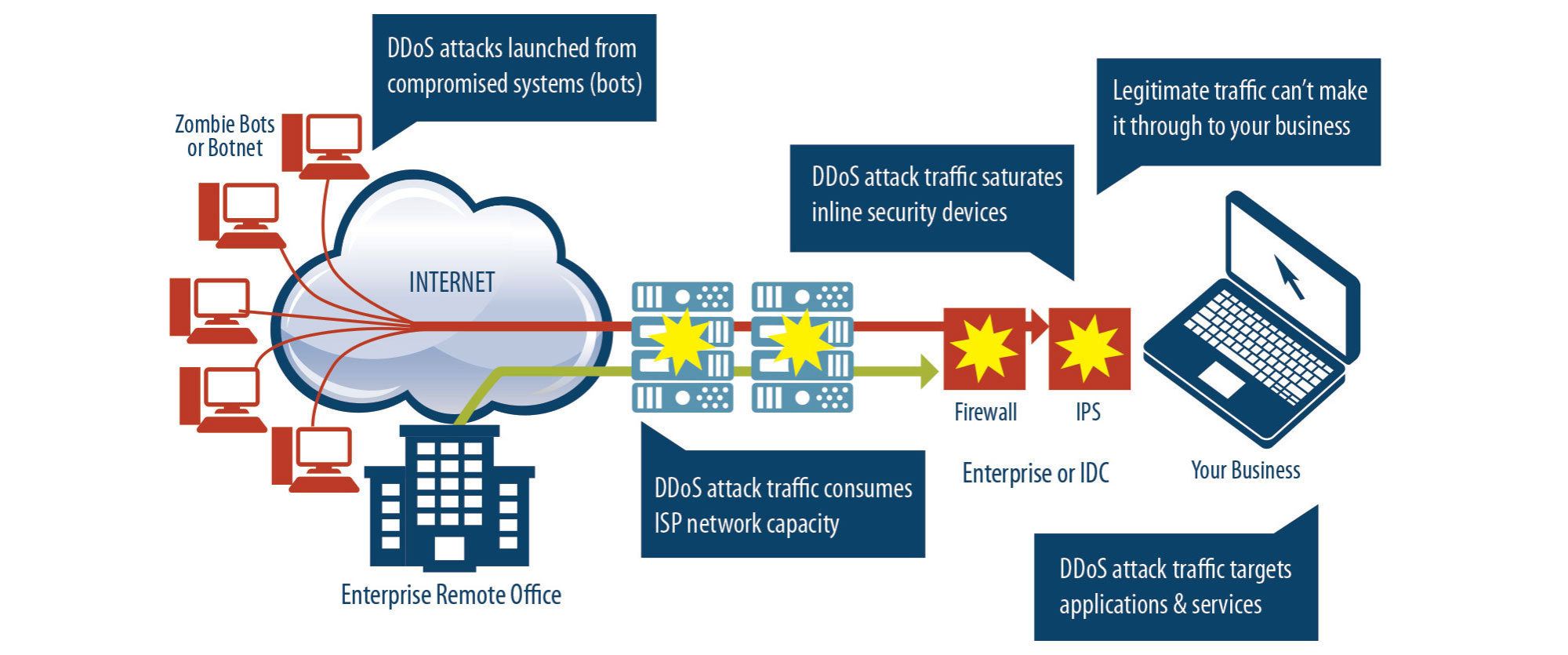
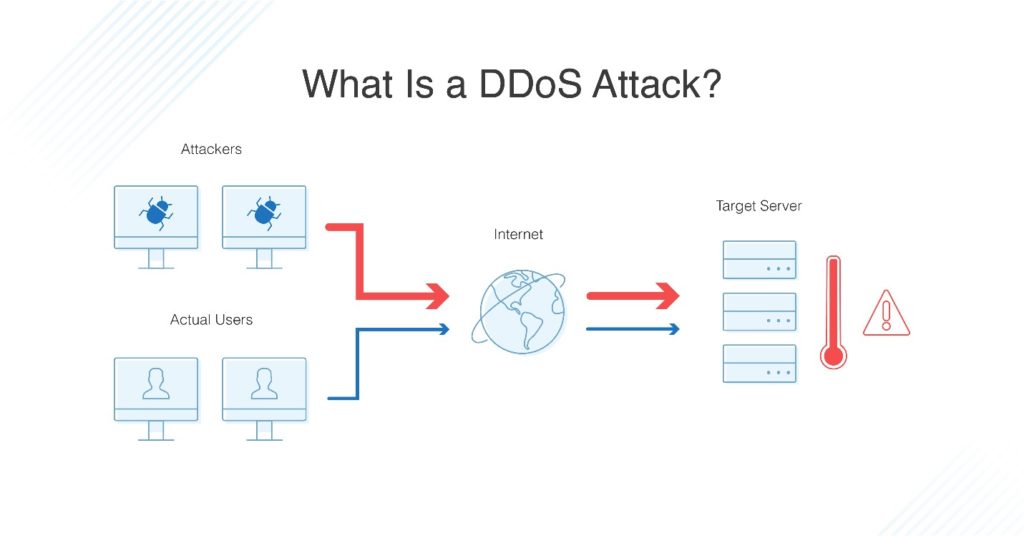
How to detect ddos. In the case of a ddos attack, the number of dns request packets will be considerably higher. A distributed denial of service (ddos) attack is when an attacker, or attackers, attempt to make it impossible for a service to be delivered. From several thousand to millions.
There are various subcategories of this attack, each category defines the way a hacker tries to intrude into the network. And this is because to detect an attack, somebody has to analyze it first in order to produce a signature. Hackers launch ddos attacks to disrupt or put down a.
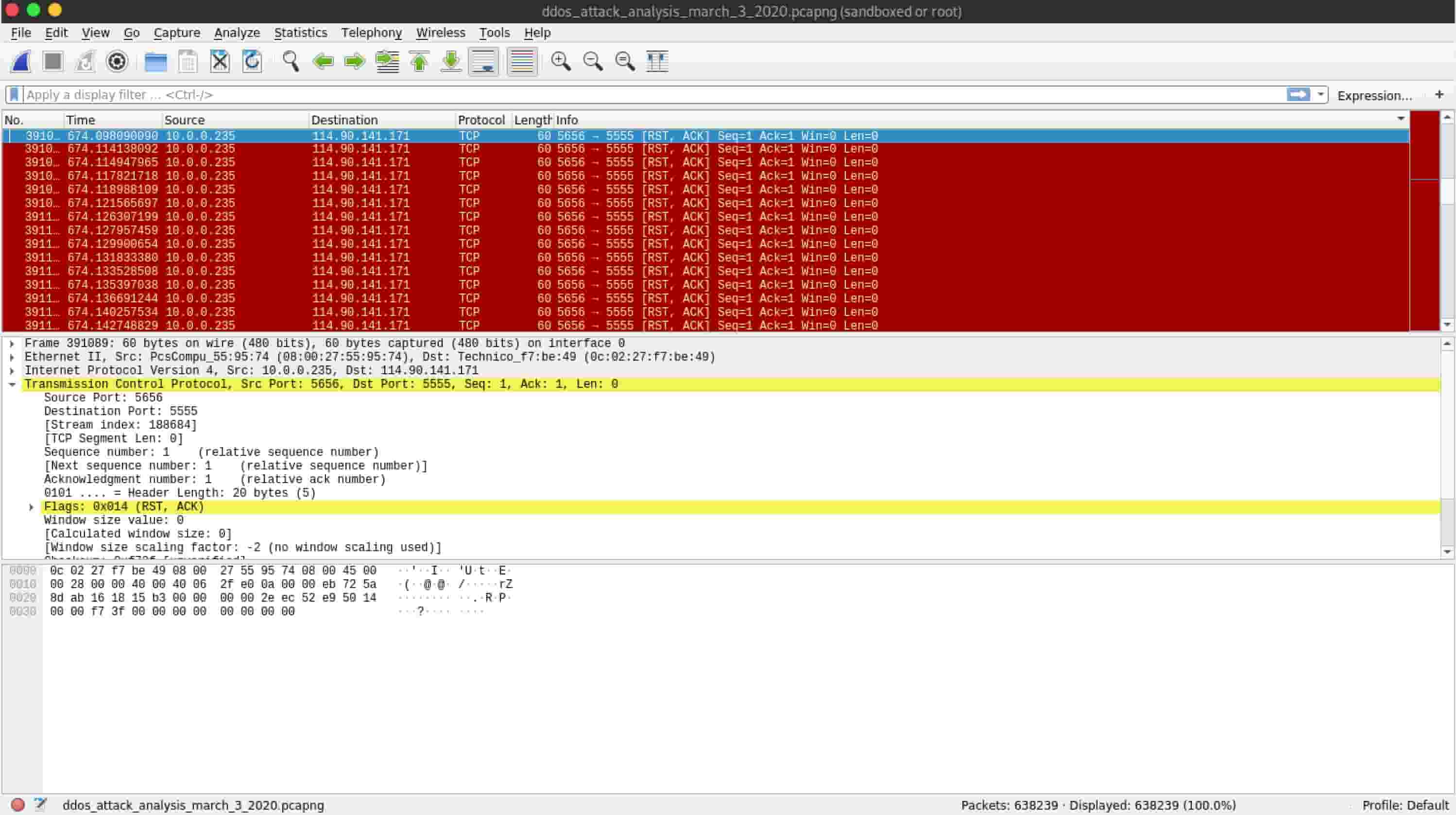
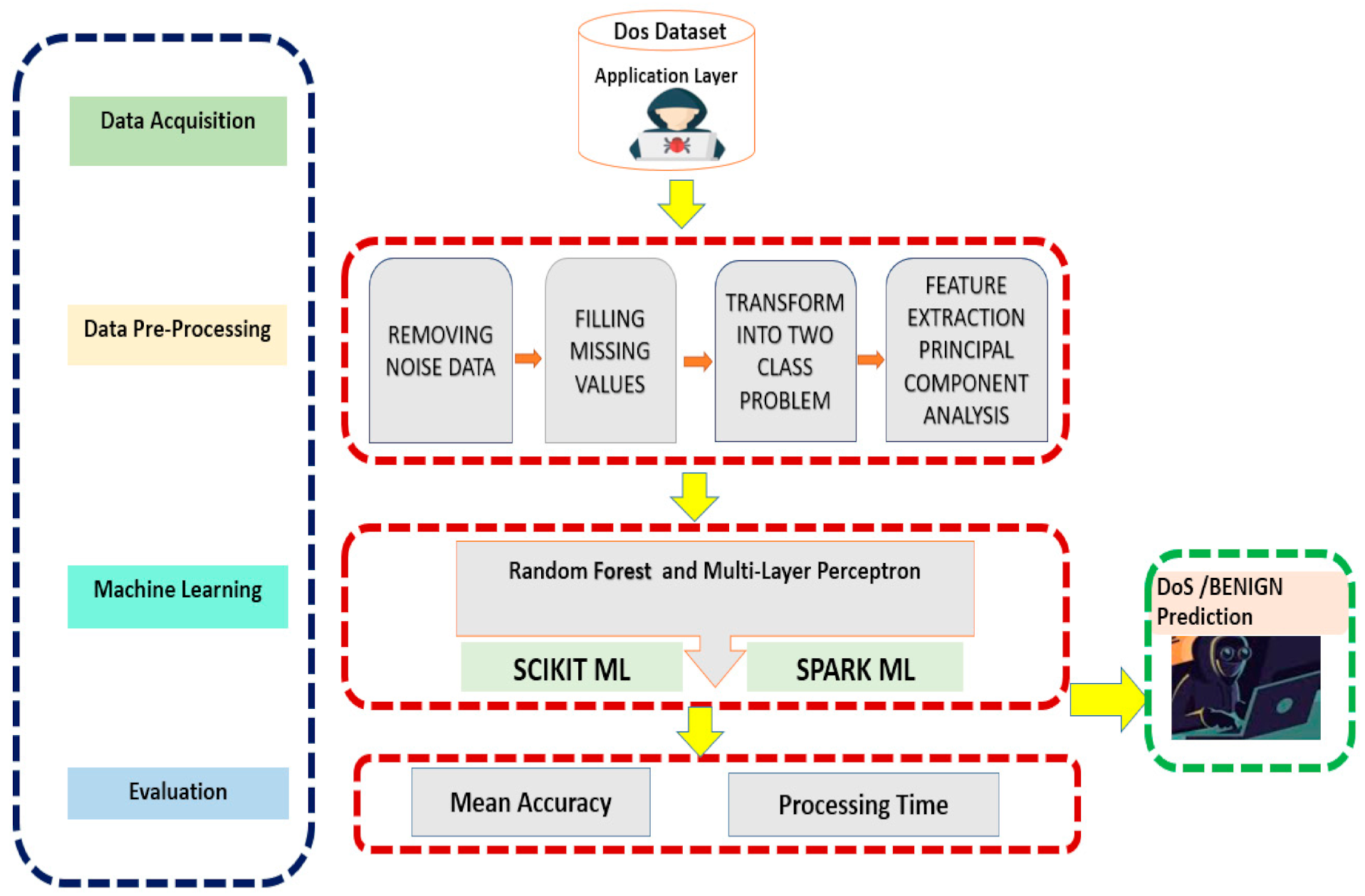
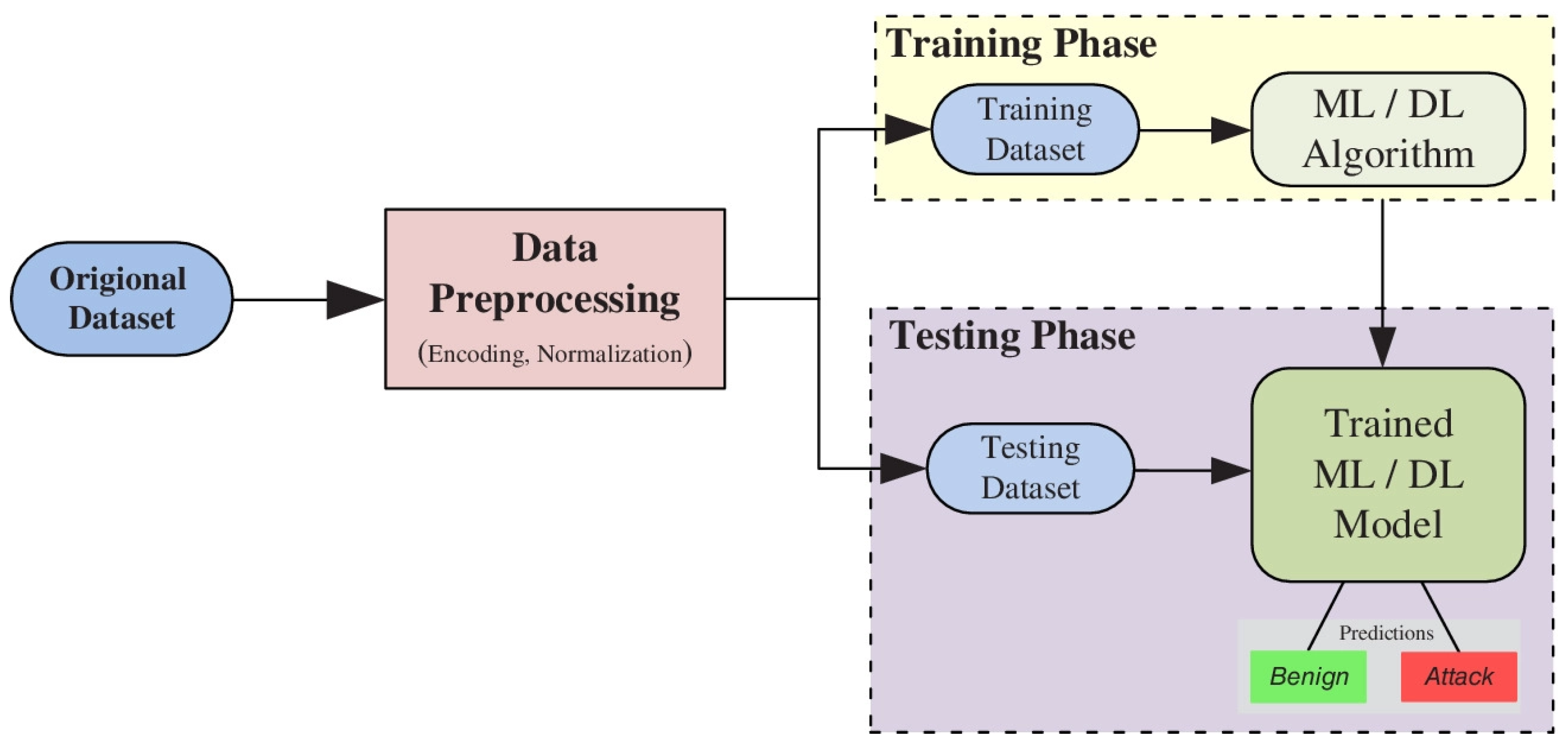
In this research, we have discussed an. There are two primary means of detecting ddos attacks: The most effective way to mitigate a ddos attack is to know when it’s happening immediately when the attack begins.
Early detection is key to mitigating these attacks effectively. While there’s no one way to detect a ddos attack, there are a few signs your network is under assault: Part of the challenge of defending against such.
There are several clues that indicate an. Distributed denial of service (ddos) attacks have increased in frequency and sophistication over the last ten years. In addition to notifying your isp, you can take.
How to identify a ddos attack? This guide will cover fundamental aspects of ddos attacks and focus on advanced methods for their. Ddos attackers often leverage the use of a.
You see a surge in web traffic, seemingly out of nowhere, that’s coming. There are a few symptoms that are a dead giveaway. If you suspect that your site is under attack, the first thing you should do is contact your hosting provider for help.
How do you know if your website just went down because of a ddos attack? We have analyzed the relevant studies and the results of the slr are categorized into five main research areas: A ddos attack is a denial of service (dos) attack that uses a botnet to flood the target with malicious traffic.
Attack surface reduction, threat monitoring, and scalable ddos mitigation tools. A truly proactive ddos threat defense hinges on several key factors: (i) the different types of ddos attack detection.
Users and prompted federal investigations was not caused by a. Here are seven key ways to enhance your. An cybersecurity attack at change healthcare—a subsidiary of unitedhealth group—that began wednesday has caused prescription delays and disruptions at a.



![【はイメージ】 Sds Calculus Module 8 Practical Applications [DVD] [Import](https://www.mdpi.com/applsci/applsci-13-03183/article_deploy/html/images/applsci-13-03183-g001.png)